Section 4
Difficulties with New Technologies
Book
Version 6
By Boundless
By Boundless
Boundless Business
Business
by Boundless
3 concepts

Forced Entry
Cybercrimes are those committed via computer networks for such purposes as fraud, identity theft, and the hacking of sensitive information.
Malware
Malware is software used or created by attackers to disrupt computer operation, gather sensitive information, or gain access to private computer systems.
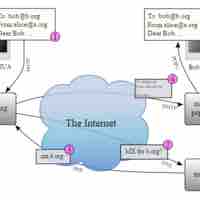
E-Mail as an Entry Point
Email represents a potential IT risk and entry point for hackers, and so IT teams must integrate appropriate safeguards.