The Now
Understanding Login Methods

Understanding login methods
Although there are countless websites, accounts, and devices, there are only a few login methods you'll need to understand to get the most from your online experience. These methods are passwords, fingerprint scanners, and two-factor authentication, and they each serve a different purpose.
Passwords
By far the most common way of accessing your digital information is through a password system. It's used by websites, devices, and accounts all around the Internet, even GCFLearnFree.org. To keep your info safe, be sure to always use strong passwords .

Passwords aren’t perfect, of course. It’s possible for someone to guess it, or you could simply forget it. Because of these disadvantages, some people prefer to use other methods whenever possible.
Fingerprint scanners
In 2013, the iPhone 5s introduced Touch ID, a method of unlocking your device by pressing your fingerprint against a sensor. Since then, fingerprint scanners have become a standard method of unlocking devices and have been included in numerous smartphones, tablets, and laptops.
Using a fingerprint scanner is convenient and saves time from having to type a passcode to unlock your device. It’s also incredibly easy to set up for the iPhone and iPad, as shown in our security and general settings lesson.
Because your fingerprint can be found on almost everything you own or touch, it isn't considered secure. However, duplicating a fingerprint is incredibly difficult , so you shouldn't worry too much about someone sneaking into your devices.

Two-factor authentication
Two-factor authentication
requires you to complete two different login methods before you gain access, such as a password and a one-time code sent to your phone or email. This means your info is more likely to stay safe, even if a thief takes your phone or learns your password.
Using a
one-time code
is simple: After you enter your password, a website or account will send a
code
to your phone or email address in order to confirm your identity. You must then enter this code into the website or account before gaining access. The biggest drawback to this method is that you must always have your phone or email ready in order to access your info. However, the additional security benefits are worth it.
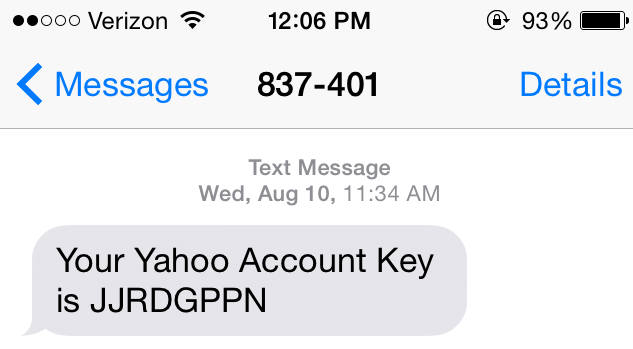
Many sites, including Amazon, Paypal, Gmail, and Facebook, offer two-factor authentication, and other sites are adopting it every day. You can learn more by reading our lesson on
two-factor authentication
.
While every login method has pros and cons, each can play a role in protecting your information. Plus, these methods will likely change as technology advances and as thieves discover more loopholes and tricks.